What are Cloud DDoS Attacks and How to Protect Against them?

DDoS is one of the fastest-growing causes of increased server downtime. While DDoS attacks are generally distributed and can take out several websites, they tend to happen when there is a large influx of traffic to a single server.
The attack may not cause the server to go down for more than a few seconds but it certainly can shut it down for long enough to force that website owner to reroute all of their web traffic to their alternative servers.
An attacker might choose a common method for attacking a server. They might choose to do it by flooding it with traffic.
This is done through a series of distributed denial-of-service attacks. The attacker sends enough requests to overwhelm a website’s server until it cannot accommodate any more traffic.
It’s called “flooding” because as more clients try to reach the target website, it causes the server to be overloaded.
A DDoS has several objectives. In the most common cases, the attackers want to overload the target website, so it cannot support any further traffic.
They may also want to shut it down for a specific amount of time, usually with the intention of causing systemwide damage. Sometimes, the attackers go so far as to try to deny access to certain Internet services.
Most DDoS attacks happen over the Internet. However, they can also happen over local networks or even on a phone line.
Many attacks happen at different times of the day because an attacker may not have an access point at your office or home.
Therefore, a traditional server backup system simply won’t cut it. You need a solution that can monitor the Internet for activity all day long. We call this a “botnet” or “DDoS proxy.”
Botnets are extremely clever attack methods. A botnet is a group of infected computers that act like a real server. They connect to several other infected computers, which are acting as relay servers.
The only difference between a regular server and a botnet is that the real server is not connected directly to the Internet, but instead to several IP addresses.
In order for a botnet to be used for an attack, a series of hops needs to occur. In the attack above, there will probably be one hop, called the “infected” computer, in addition to a few indirect connections.
The infected computer serves as a relay for the other hops. This way, when the first attack occurs, the other hops join in and help spread the attack. It’s much like how a fire has several lines of fire, with each connection on its own firefighting engine.
Some DDoS attacks happen very quickly. In fact, they can occur in a matter of seconds! Some attacks occur in short bursts, while others can go on for hours or more.
There are also DDoS attacks that are less common, where the attacker targets a single server, such as a common Web hosting site, or a single data center.
If you are wondering what a modern-day DDoS looks like, it’s much like the viruses and worms that we have been dealing with for many years. They spread rapidly, they can damage or destroy data and they leave servers vulnerable to attacks.
Now that you understand what a modern-day DDoS looks like, hopefully, you will not be the next victim. If you are a server administrator or someone who works on network infrastructure, it’s important that you understand DDoS and what to do in the event of an attack.
What are cloud DDoS attacks?
It is a new attack that uses massive amounts of data to send spam and cause intentional damage to websites. A Cloud DDoS refers to a DDoS (directed online attacks) that takes place over a network of computers that are connected to the Internet.
The term ‘Cloud DDoS’ is used to refer to several different attacks that take place via cloud services. These include distributed denial of service (DDoS attacks), server overloads, and system overloads.
There are several reasons why an attacker may want to use a Cloud DDoS. Some reasons to attack a website could include reducing costs, increasing traffic, increasing brand awareness, and preventing the target site from functioning.
Many people may be wondering exactly what an attacker needs to do in order to trigger a denial of service attack. Well, a typical DDoS involves sending thousands of fake messages to increase the website’s traffic.
Once enough traffic is reached then the website will enter a state where data will be purged and no data will be recovered.
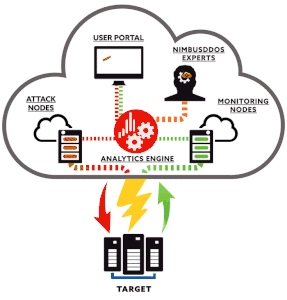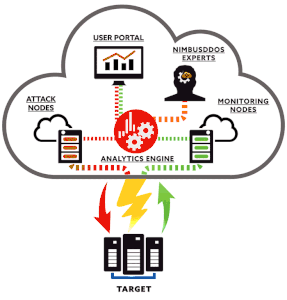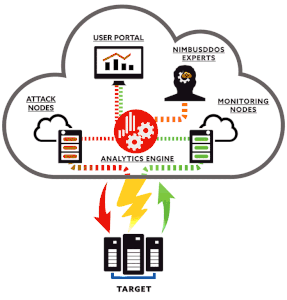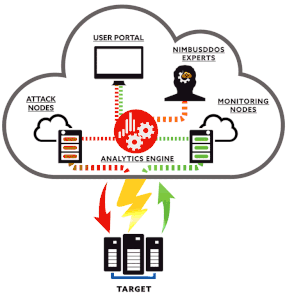
Some common tools used for this include scripts and automated processes. In order to defend against these attacks a Cloud provider needs to have a robust DDoS prevention plan.
Some attacks cause so much traffic that the website goes down for days while it is being repaired. In some cases, a simple system refresh will prevent an attacker from sending further attacks.
Another common type of Cloud attack is a Stateful DDoS. This is where a DDoS can originate from anywhere on the internet.
The way it works is that a targeted website will trigger a Cloud attack. These attacks are very hard to defend against and oftentimes even the best Cloud provider is not able to stop them.
So if you are using cloud or if you’re looking to use cloud in your business then you need to be aware of the potential dangers.
How to protect against cloud DDoS attacks
There are some simple steps that you can take to protect your website from cloud DDoS attacks. The first step a Cloud provider should take is to analyze the threats that it may be facing. If the Cloud provider is not expecting the attacks then it may not be able to prevent them.
Cloud providers will often offer DDoS prevention through systems like Google Cloud Security. However, even with this protection there are still chances that an attack will occur.
For instance, if you are using Google Cloud to protect your website then you are going to need a modern SSL certificate. SSL certificates provide proof that the website has been authorized by a trusted third party.
If an attacker can create a rogue SSL certificate then it will allow them to login and take control of your account and any information contained on it.
A Cloud provider also offers protection through the Use of HTTP response headers. HTTP response headers are used during a web request to provide details about the way to proceed with the requested information.
If an attacker can determine which keywords are used in the request then they will be able to trigger a denial of service (DDoS). If this happens then the site will be inaccessible until the problem is resolved.
Using cloud DDoS protection
Cloud DDoS protection is a powerful and new method of mitigating the risk of network attacks. It is a form of self-defense mechanism that utilizes the distributed response of a cloud computing infrastructure.
A DDoS attack is the targeted delivery of unusually large requests to a service, typically through the internet. The resulting outage can have serious consequences for the operations of the target organization.
The first benefit of using cloud DDoS protection is the prevention of attacks. Attacks are prevented because traffic is passing through a multi-layered security service layer.
This ensures that no single point in the system is allowed to cause attacks. In addition, no single server is allowed to be attacked, and no port-forwarding rules are enforced. This form of self-defense is achieved by the use of counters.
The second benefit of using cloud DDoS protection is the mitigation of damage. When attacking traffic is redirected through the web defense mechanism, the traffic is halted before it reaches its target.
Furthermore, the traffic is not allowed to use any of the attacking ports, so any malicious programs attempting to use them will be blocked.
In addition, if any of the attacking traffic uses a port that is not allowed, then the server will be unreachable until the port is mapped correctly using the appropriate IIS control panel.
Cloud-based DDoS attacks can be prevented by using DDoS mitigation services. These services are run by experienced professionals who have a proven track record in dealing with the latest attacks.
They will also know the best ways to protect an enterprise from these attacks, as well as the methods that might be successful against it. This is important because an attack can come at any time.
The most important benefit of using cloud solutions is that they provide real-time protection. An organization’s valuable data cannot be compromised in any way.
Therefore, companies should not overlook the potential risks posed by cloud-based applications when deciding whether to invest in them.
Enterprises that make the decision to deploy these services are doing themselves a huge favor because the risk of a DDoS attack is higher than using traditional infrastructures. Hence, the probability of a successful attack is much higher.
Another major benefit is that businesses and organizations do not need to take all the risks related to security when running their applications on the cloud.
In addition to ensuring that data is secured, organizations that use cloud applications will also experience fewer complications in terms of security compared to companies that do not use this technology.
When a malicious software application is launched on a targeted server, it will likely perform a task automatically, which means that it will spread itself to hundreds or even thousands of servers on the network.
However, if an IT administrator is monitoring the environment and keeping a watchful eye on the application, he or she can close all the vulnerable connections right away before the application starts to spread its payload.
Obtaining the right cloud computing security is essential in the present times. While there is no denying that this technology has brought about massive changes in the manner of how business transactions take place on the web, it is also essential for companies to realize that it is not enough to make their web services immune from attack.
If they choose to invest in cloud computing security, they must do so because they want to ensure the best results at any cost, rather than just focusing on cost reduction. Otherwise, they may find that they are spending too much money unnecessarily in the process.
Why you should use BlockDos cloud DDoS protection
BlockDos cloud protection delivers well-rounded security with a blistering response time. Cloud nodes of BlockDos are very responsive and well managed so you don’t have to worry about downtime.
BLockDos ddos protected cloud is powered with multiple hypervisors and its SAN storage is protected by central RAID-10 which makes it the best solution for businesses hoping to achieve scalability
