Get Ultimate Protection with GRE Tunnel
Overview:
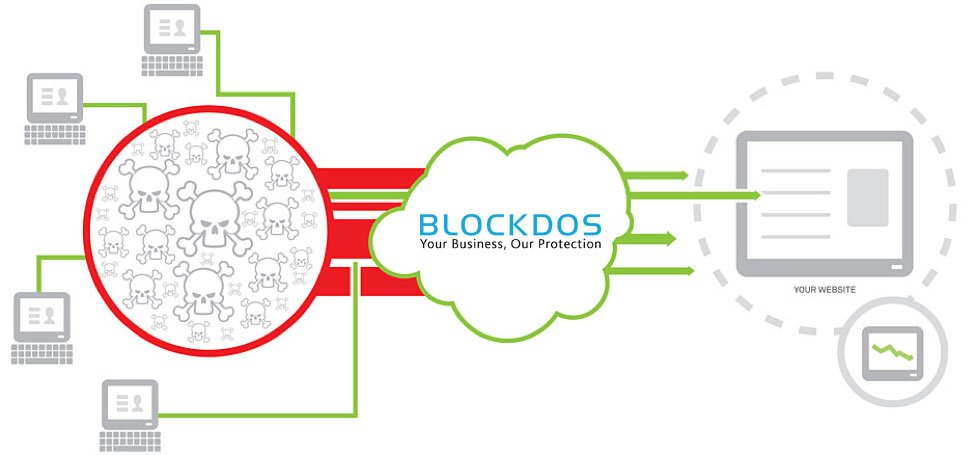
By using Generic routing encapsulation (GRE) tunnel, BlockDOS is able to offer you with an enterprise-grade communication protocol which establishes direct end-to-end connection between any network infrastructure. This allows you to use multiple protocols network backbone which supports a single protocol only. On top of this, GRE tunnel has a lower footprint than rest of the high resource demanding alternatives like IPSec VPN. Most importantly, GRE tunnel is a solid workaround for networks that support a limited number of hops. BlockDOS GRE tunnel makes use of encapsulation to establish direct connection to your server with comprehensive DDoS mitigation solution deployed at the edge of your network.
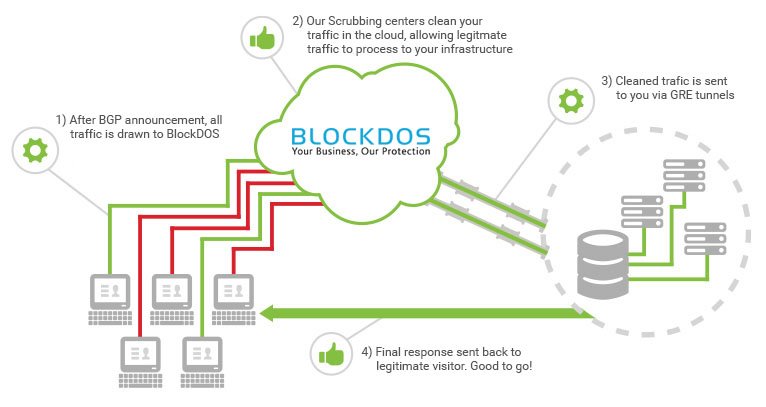
How it works?
When you sign up for our GRE tunnel protection, we will assign you a secure IP from our protected IP range for routing traffic. This would allow a GRE tunnel to be established between your servers and our network. Once GRE tunnel is setup properly (which is usually within minutes), it is used to route clean traffic from our network to your server and vice versa. The next step involves you pointing your DNS to our secure IP.
Once the DNS is propagated, within minutes if the TTL - Time to Live - is kept within 300 seconds, all traffic to your website flows through BlockDOS network. It’s inspected by our DDoS pattern recognition system and filtered through hardware firewalls. Once we have produced “clean” traffic, we pass that onto the GRE tunnel which connects our service directly to your website.
So if you are interested in protecting your critical network infrastructure, please contact us today for a free custom quote.