THE ORGANIZED CHAOS OF CHAOTIC CYBER ATTACKS
A view of the cyber attacks carried out against the U.S. within a 45-minute span.
These days it’s not just the air flight route maps available out there for the aviation industry enthusiasts, there’s something more interesting that’s being mapped. Cyber attacks maps. Yes, now you can track in real-time, who’s attacking who in the cyberspace.
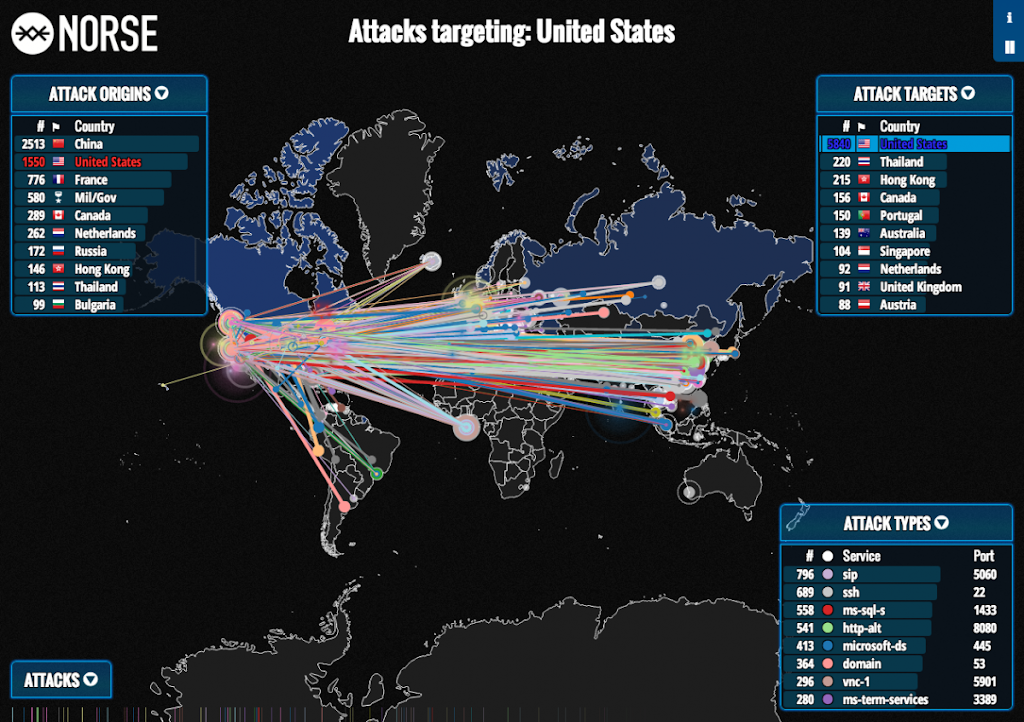
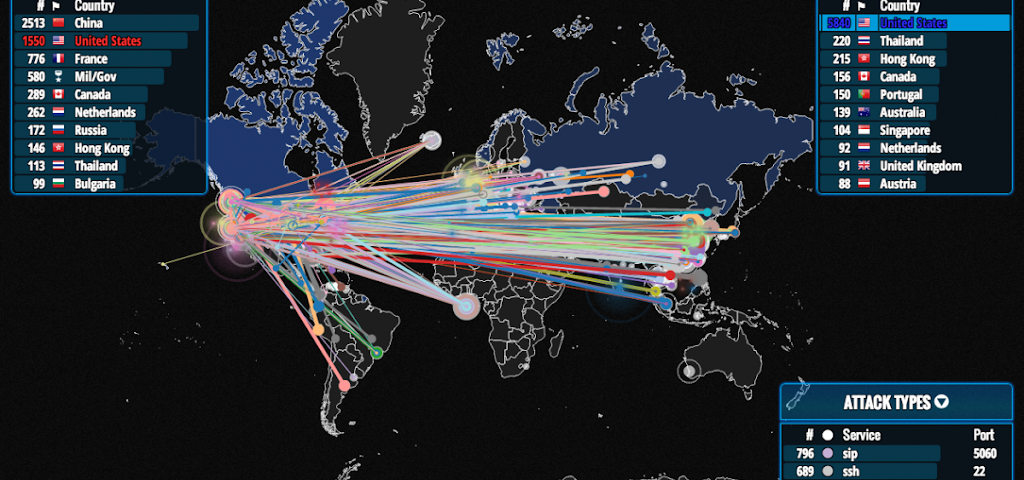
U.S.-based computer security firm Norsehas released a real-time animated map that illustrates ongoing cyber attacks around the world. Without a doubt, the U.S. is getting constantly hammered by hackers.
In just 45 minutes, the U.S. was the victim of 5,840 cyber attacks.
Within that span of time, the U.S. suffered from 27 times more cyber attacks than Thailand, the second most targeted country. Thailand was the target of only 220 cyber attacks during these 45 minutes.
The Norse map does not represent all hacking attempts in the world. Instead, according to Smithsonian Magazine, the map relies on a Norse honeypot network — a network purposefully designed to detect hacking — to provide a representative snapshot of global hacking attempts.
In actuality, there are orders of magnitude more hacking attempts on any given day than recorded by Norse. For instance, there are an estimated 20 million attacks per day against locations within Utah. There are 10million daily hacking attempts against the Pentagon alone.
China is responsible for the vast majority of these attacks. Within the 45-minute span, China accounted for 2,513 attacks. The U.S. accounted for the second highest number of attacks, with 1,550 attacks originating within America. However, a number of American attacks targeted computers elsewhere in the United States.
It is likely that these intra-U.S. attacks are the result of “zombie computers” — computers that have been compromised by a hacker and carry out attacks at the hacker’s discretion. Chinese cyber attacks are highly damaging to both the U.S. economy and national security. China is currently developing a new plane that is modelled after stolen plans for the U.S.’ F-35 fifth-generation plane.
As well as letting the viewer watch the war game that’s taking place and that too in real-time, it’s not all just fun watching it, it’s more serious than that. Something ought to be done to stop this madness. Security firms all over the world are working hard to find solutions better and better to curb this nuisance and bring peace to the cyber-space. Stay connected for more news on how these attempts are being made.
Source:
Business Insider/Military & Defence – Norse Corp.
Picture Screen shot map.ipviking.com